gSTM, the Gnome SSH Tunnel Manager, is a front-end for managing SSH-tunneled port redirects. It stores tunnel configurations in a simple XML format. The tunnels, with local and remote port redirections, can be created, deleted, modified, and individually started and stopped through one simple interface. It is useful for anyone wanting to securely access private services over an encrypted tunnel.
Install Gnome SSH Tunnel Manager in Ubuntu
First you need to download the .deb package from here using the following command
wget http://kent.dl.sourceforge.net/sourceforge/gstm/gstm_1.2_i386.deb
Once you have the gstm_1.2_i386.deb package you need to install this using the following command
sudo dpkg -i gstm_1.2_i386.deb
This will complete the installation.
If you want to open this application go to Applications—>Internet—>gSTM

Once it opens you should see the following screen
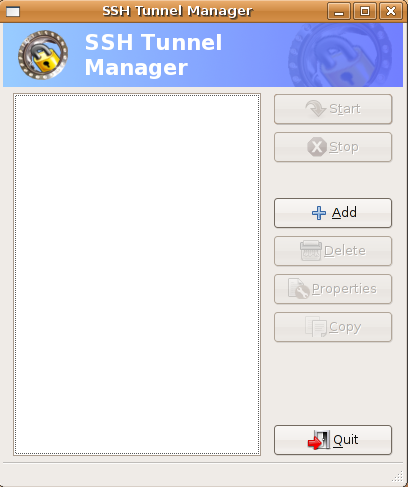
If you want to add ssh tunnel you need to click on add now you should see the following screen here you need to enter the name of the tunnel and click ok

Once you click ok you can see the following screen here you need to fill all the required detailed for your host and click ok

If you want to add a port redirection you need to select add under portforwarding in the above screen
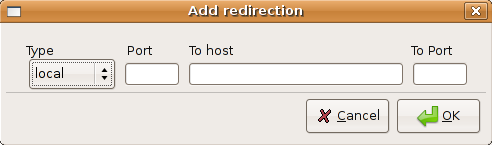
Once you click on ok you should see the following screen if you want to connect to SSH tunnel select your host and click on start it should start connecting to your host

Examples
Remote Desktop
Remote Desktop to various Windoze servers in the private LAN. Although Remote Desktop supports some degree of encryption itself and you can easily create a port-forward in your firewall. First of all you don’t want to create a port-forward for every desktop you want to reach. Second and most important, you don’t want the Remote Desktop ports open for the world to see… for obvious security reasons.
Secure POP3
If you are running a POP3 service on your *nix router/server you are probably aware of the fact POP3 is an unencrypted, plain-text protocol. Hypothetically this means any ‘man-in-the-middle’ is able to read your username, password and e-mail content. Obviously, on your private LAN this isn’t a problem, however you might want to read your mail over the internet one day…
One solution would be to install pop3s or better yet, imaps. However there is another way, without having to install additional services: an SSH tunnel.The way it works is, you connect to your router/firewall through ssh and set up a portredirect over it (ie. a tunnel). You can then connect your e-mail client to your localhost. The connection will then be redirected over the encrypted SSH connection to your POP3 service. Et voila, a secure POP3 connection.